# Decryption of TLS sessions
Goal
- Using Wireshark to decrypt (HTTPS) web traffic.
Used hardware
- 1 laptop with Microsoft Windows
Used software
- Wireshark 3.2.1
- Firefox or Chrome
Setup
Getting started
- Set the environment variable SSLKEYLOGFILE.
More information about TLS (opens new window)
We will use Windows Powershell to complete this task.
$env:SSLKEYLOGFILE "C:\Users\Student\Desktop\keys.txt" Get-ChildItem env:SSLKEYLOGFILE Name Value ---- ----- SSLKEYLOGFILE C:\Users\Student\Desktop\keys.txt1
2
3
4
5
6- Create the file keys.txt on the correct location.
We will use Windows Powershell to complete this task.
New-Item C:\Users\Student\Desktop\keys.txt1Reboot your system.
Start Wireshark and capture traffic.
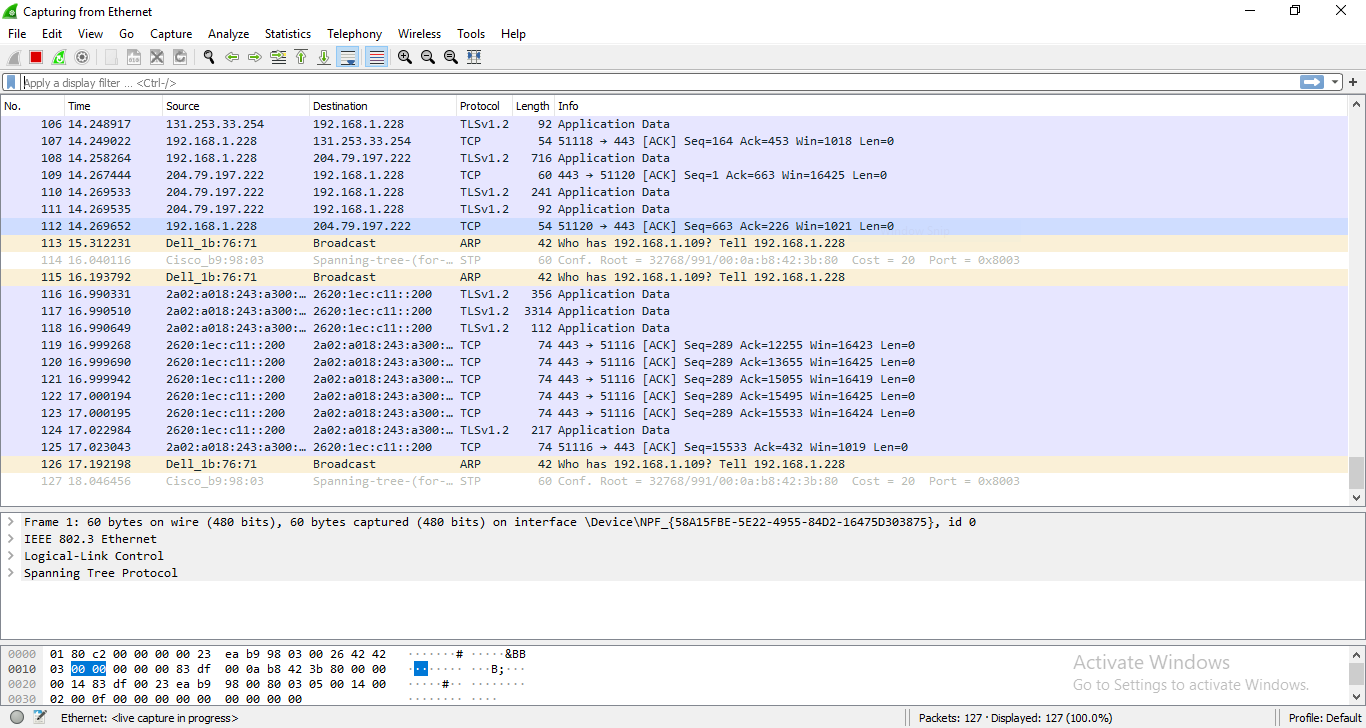
- Open Firefox and go to a website.
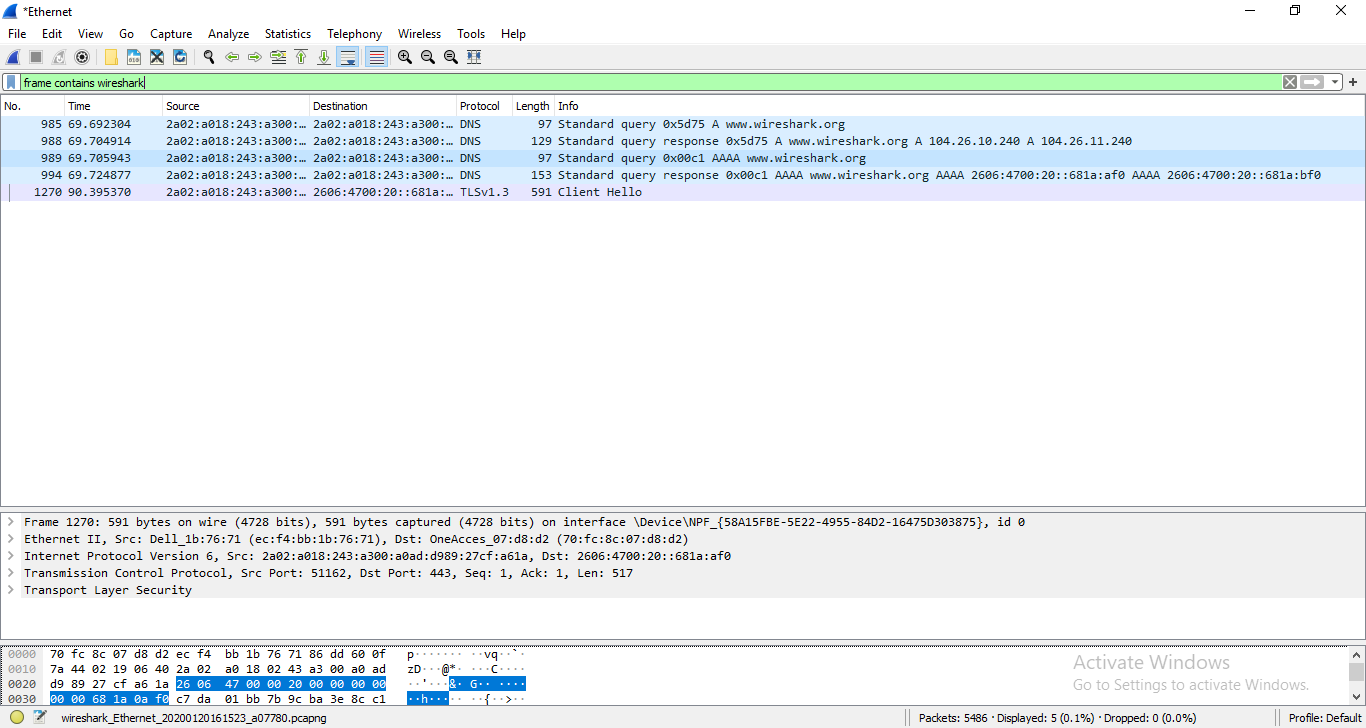
- Stop the capture and look for the correct session.
First, we look for frames that are containing the word "wireshark".
Afterwards, we select the correct stream.
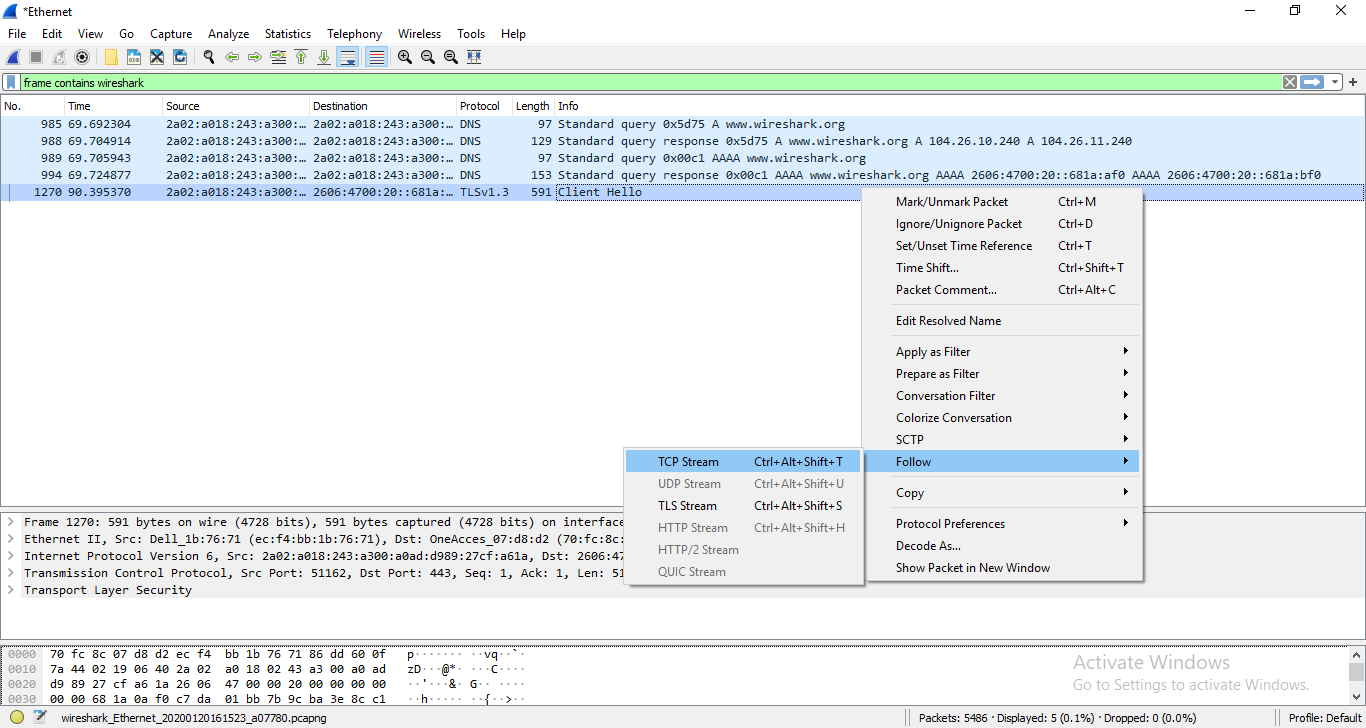
This stream is still encrypted.
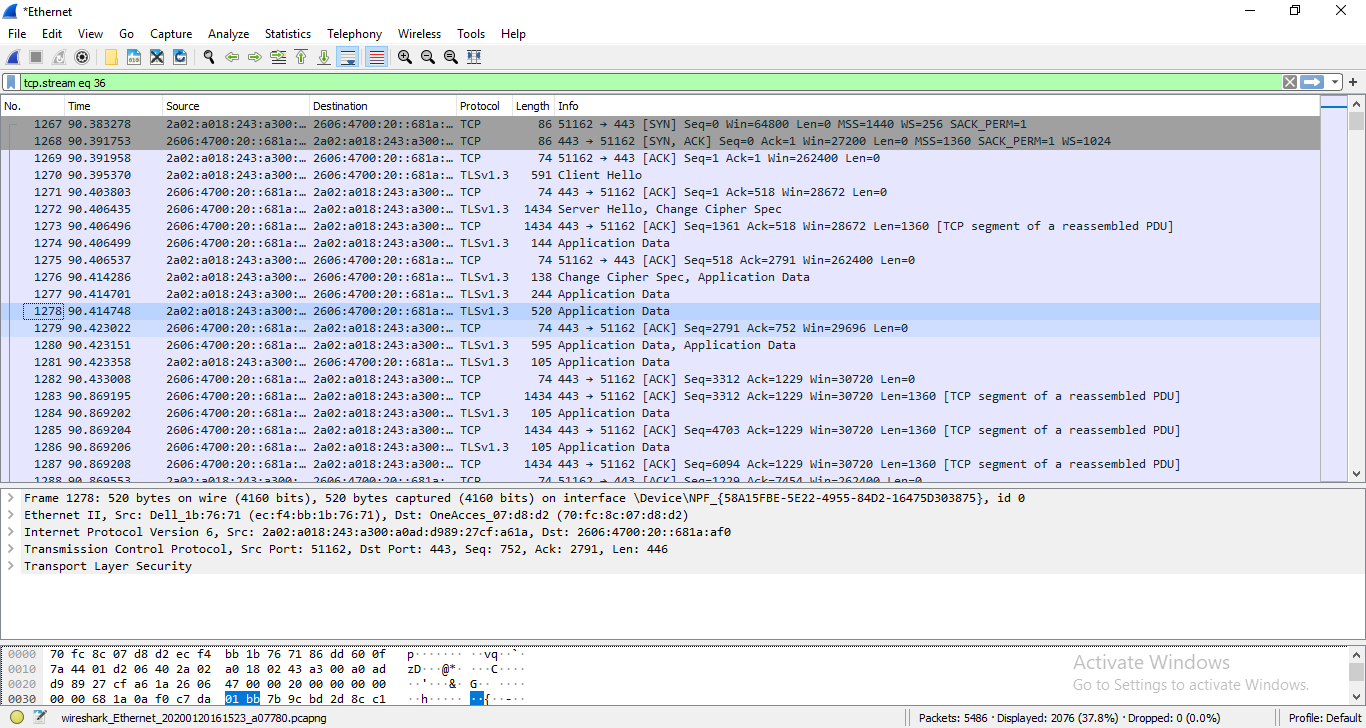
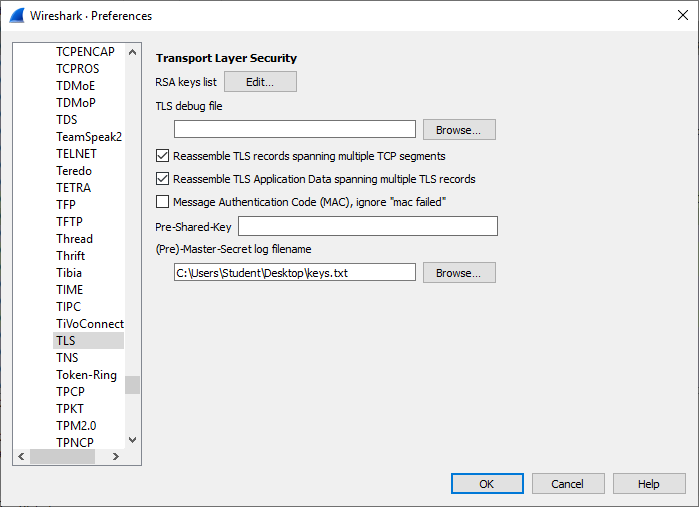
- Configure the key log file in Wireshark.
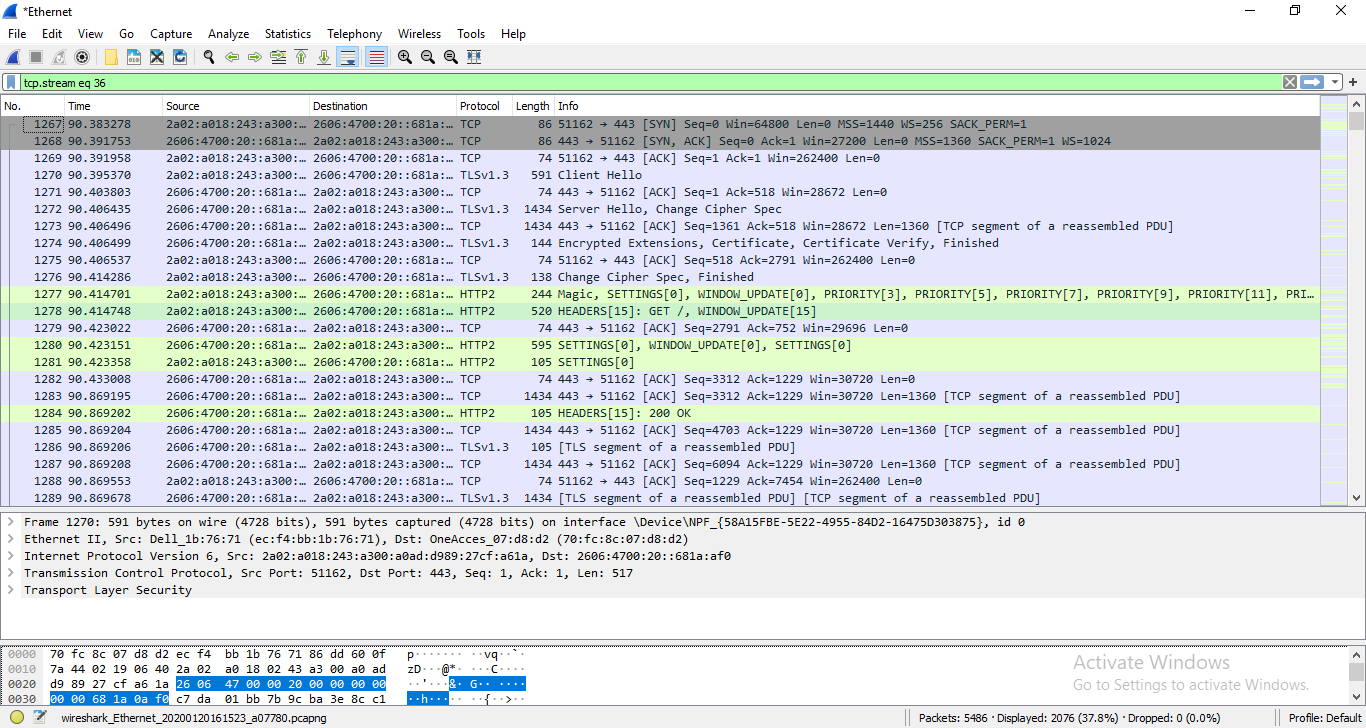
- Look at the result. (TLS decrypted).
Conclusion
- Once Wireshark and your environment are set up properly, it is a piece of cake to view decrypted data.