# ARP spoofing (MITM)
Goal
- Intercept the communication between 2 devices in a switched network.
Used hardware
- 1 laptop with Kali Linux
- 2 devices (Computers, laptops, ...)
Used software
- Kali Linux (2019.4)
Setup
Getting started
- Get an overview of your network. (Kali Linux)
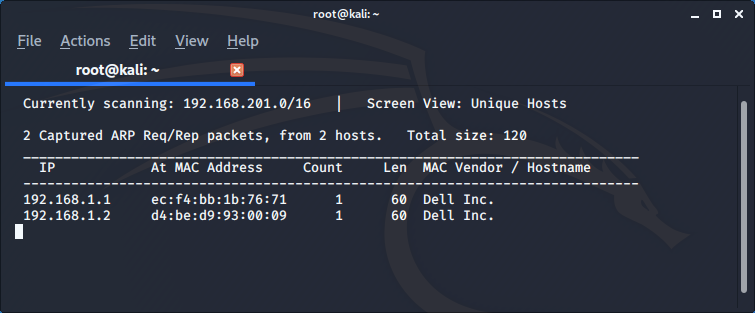
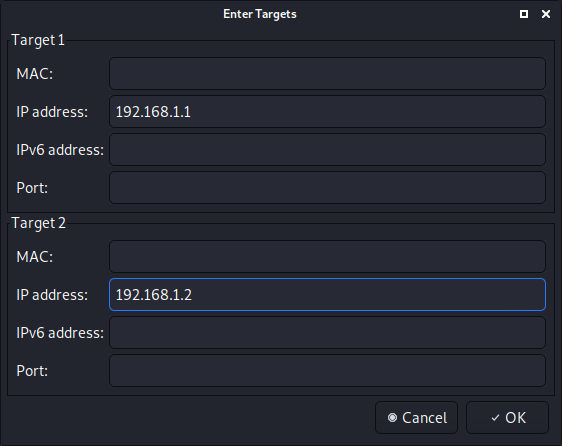
The result shows us the client (192.168.1.1) and the server (192.168.1.2).
- Start the communication between the client and the server.
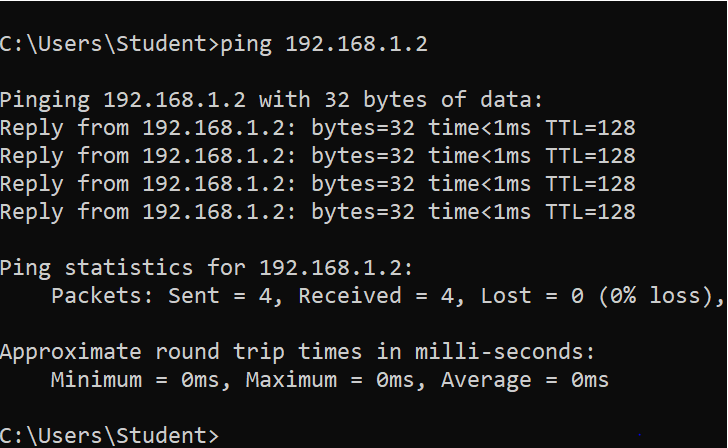
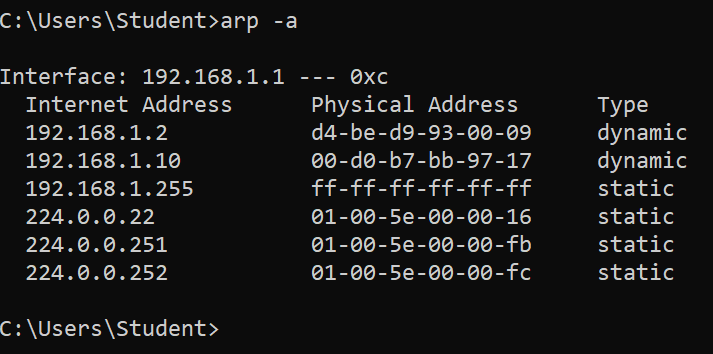
- Look at the MAC address table of the client.
- Start Wireshark (Kali Linux)
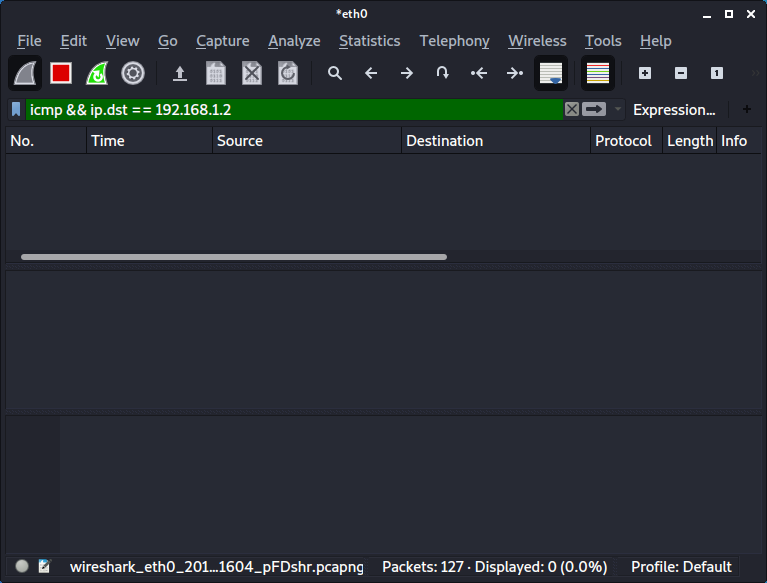
The result shows us no ICMP traffic destined for the server (192.168.1.2).
- Set IP forwarding. (Kali Linux)
IP forwarding allows an operating system to forward packets as a router does or more generally to route them through other networks.
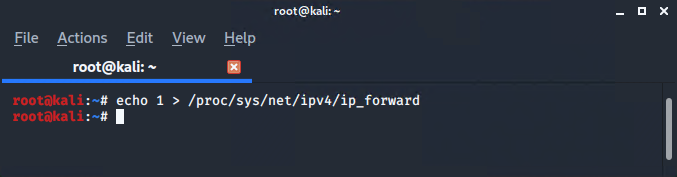
Launch the MITM attack. (Kali Linux)
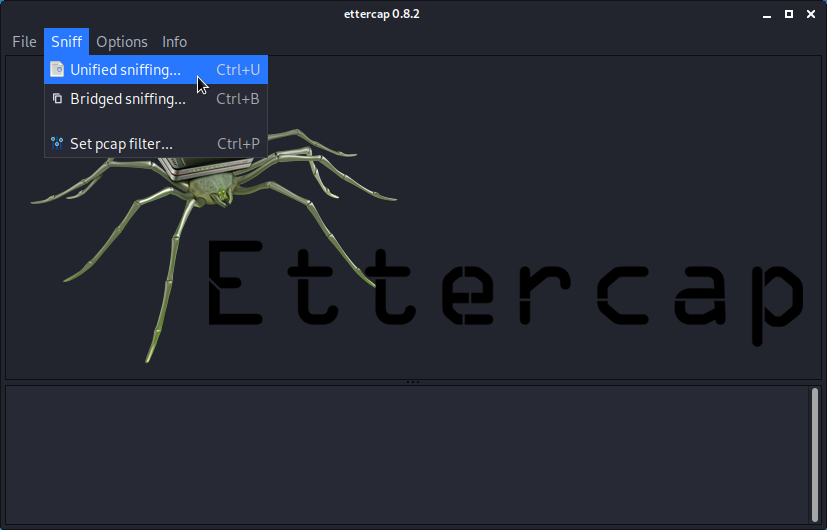
- Start Ettercap.
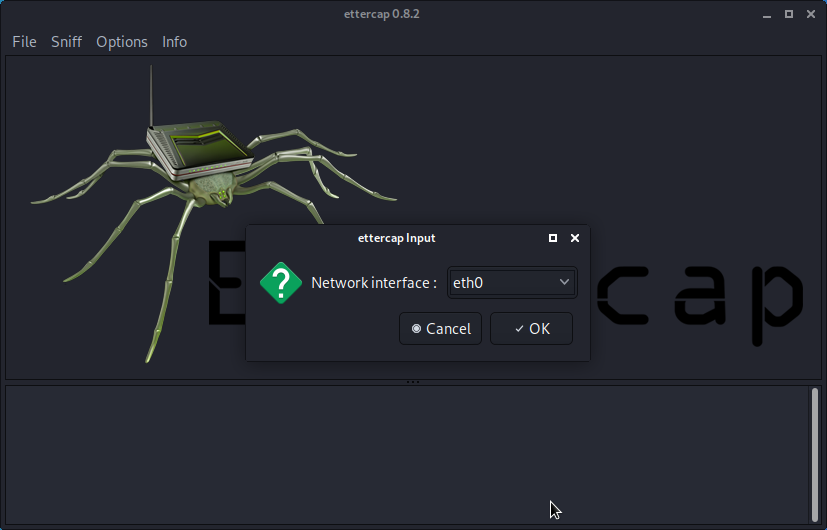
- Select the correct sniffing method and interface.
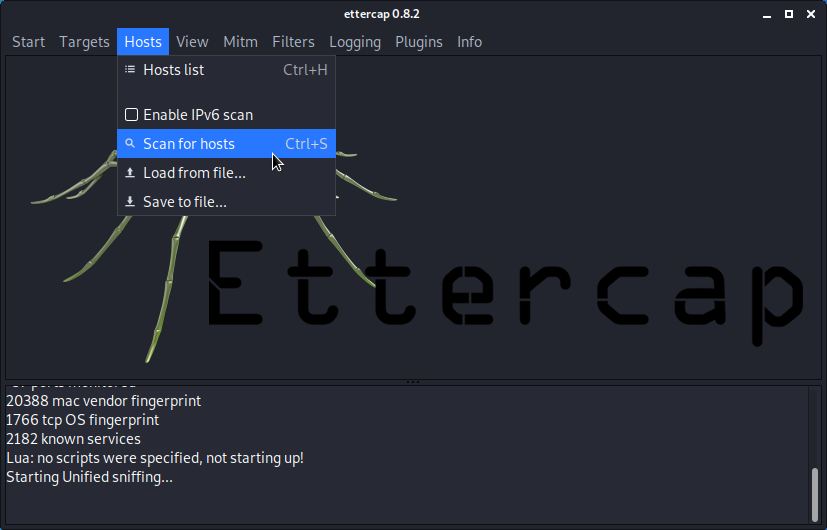
- Select the hosts (via a scan or manually).
- Start the attack.
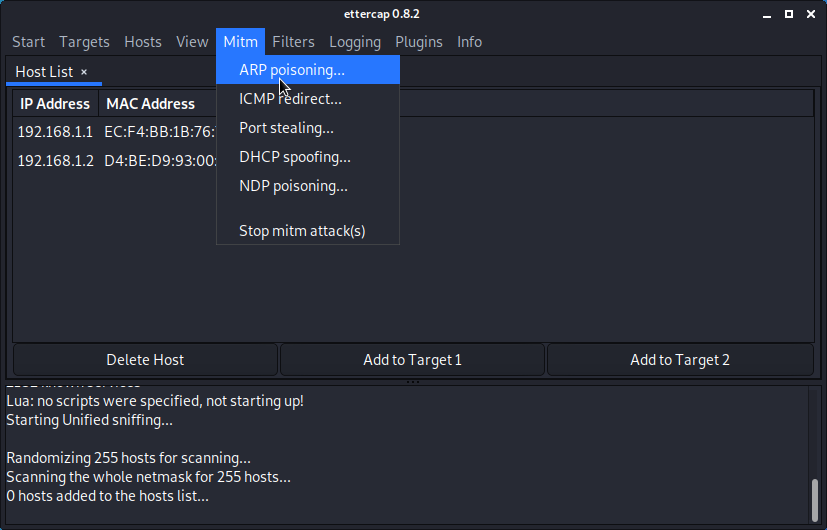
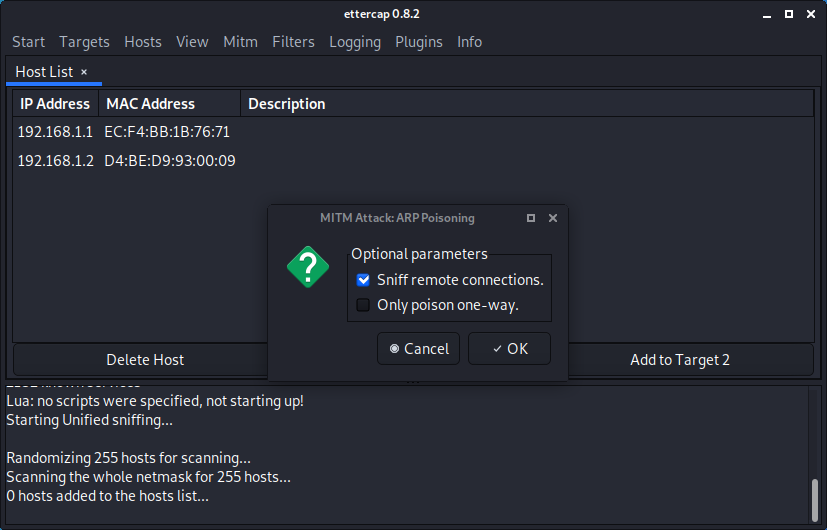
Verify if the attack was succesfull.
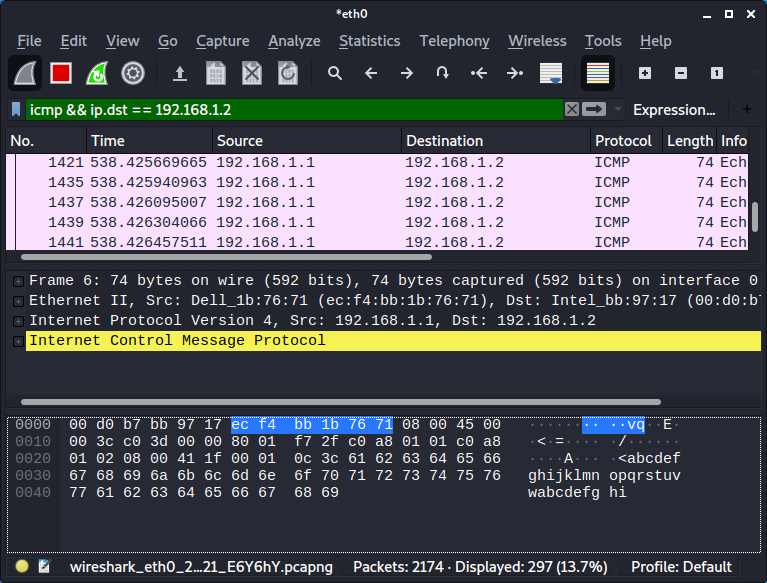
We are now capturing the traffic between the client and the server.
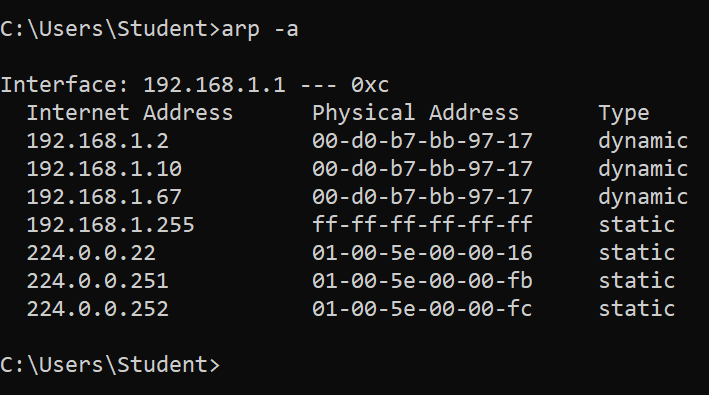
The MAC address table of the client is poisonend. (192.168.1.10 is our Kali)
Conclusion
- A man-in-the-middle attack (MITM) is easy to establish and hard to detect.