# Capture packets on a remote system
Goal
- Wireshark captures traffic from your system’s local interfaces by default, but this isn’t always the location you want to capture from.
Used hardware
2 laptops with Microsoft Windows
Note: This feature is only available on Windows. Wireshark’s official documentation recommends that Linux users use an SSH tunnel.
Used software
- Wireshark 3.2.0
- WinPcap 4.1.3
Setup
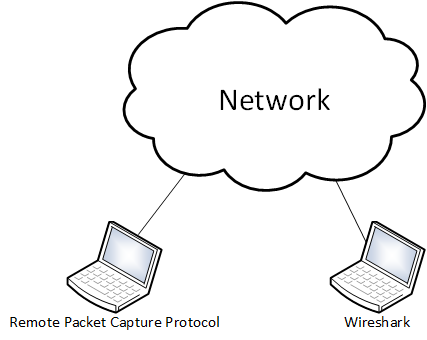
Getting started
- Install WinPcap on the remote system.
More information about WinPcap (opens new window)
- Start the Remote Packet Capture Protocol service on the remote system.
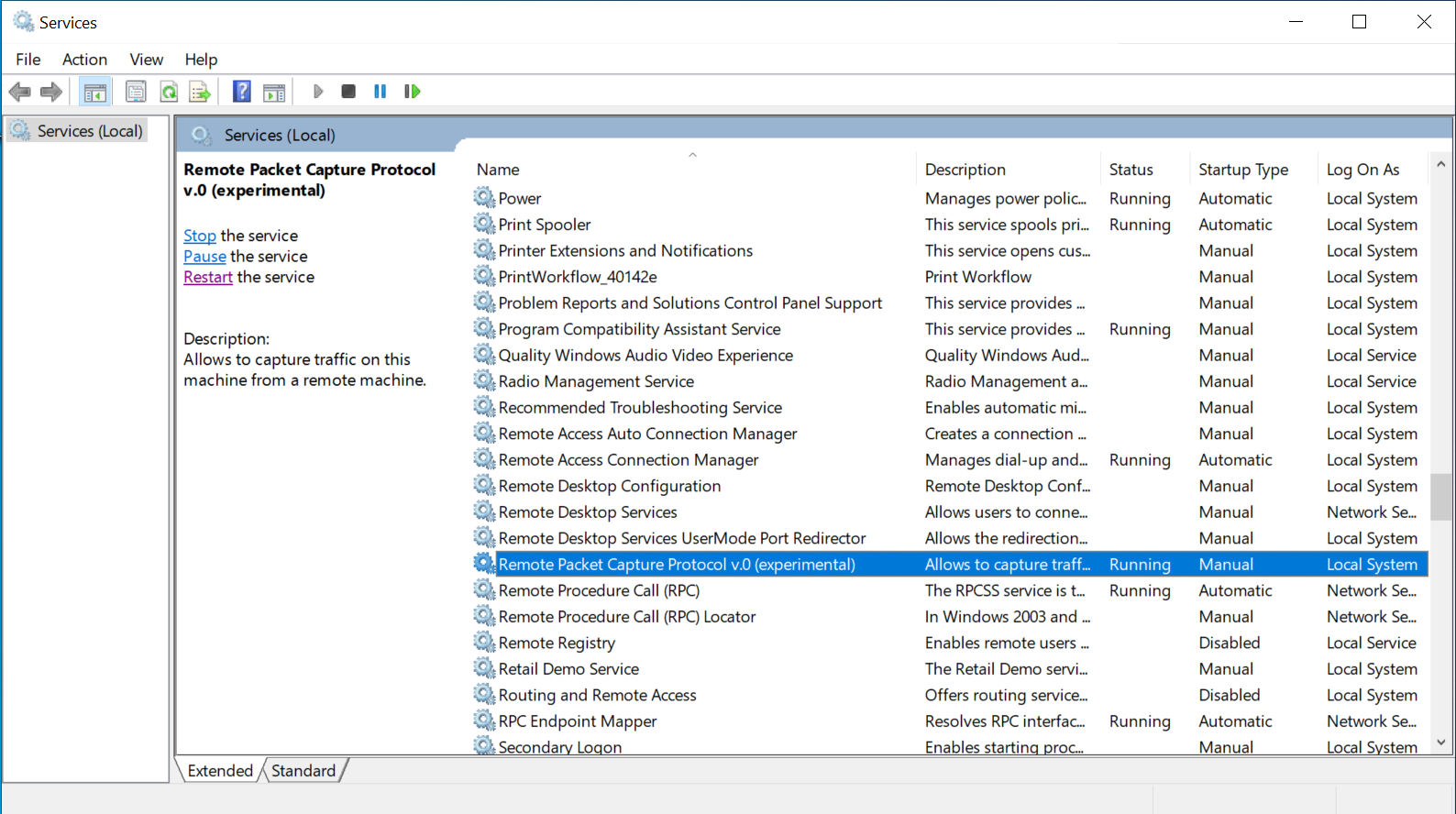
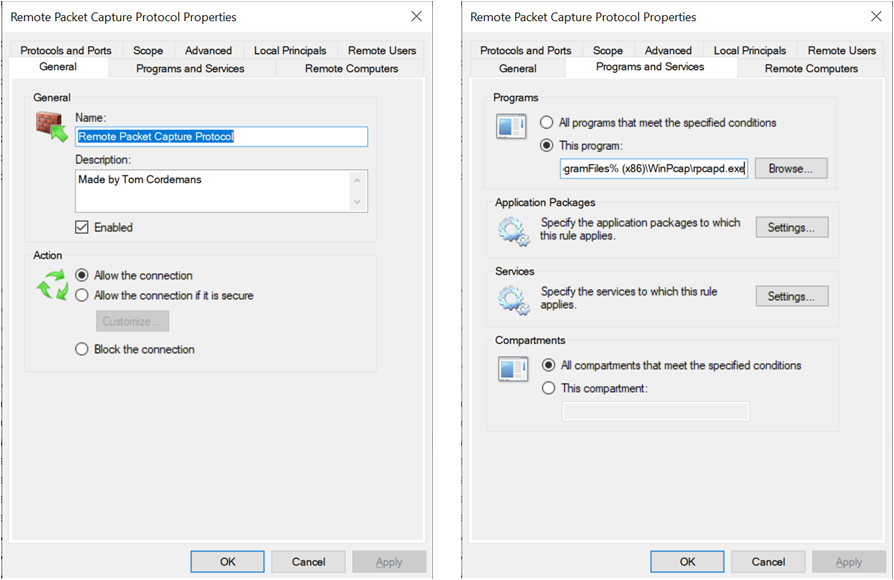
- Add a firewall rule to the host-based firewall of the remote system (if necessary).
- Open Wireshark on your local system and select "Capture" followed by "Options".
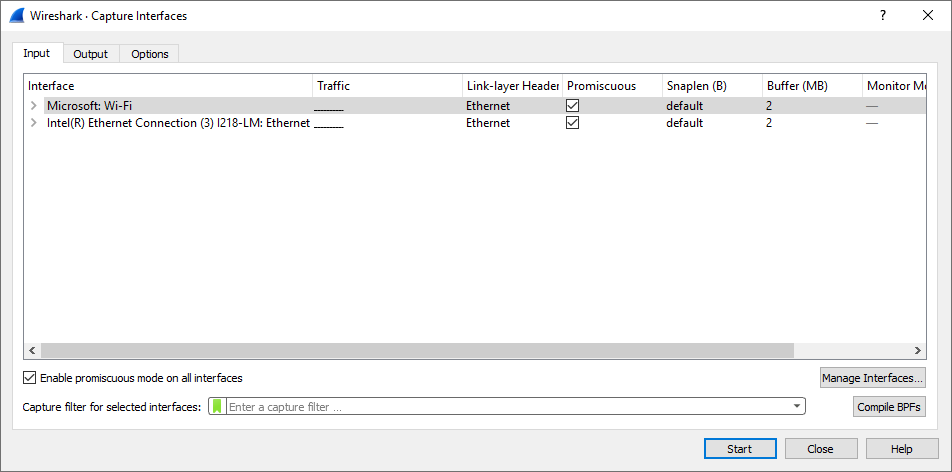
- Select "Manage Interfaces" followed by "Remote Interfaces".
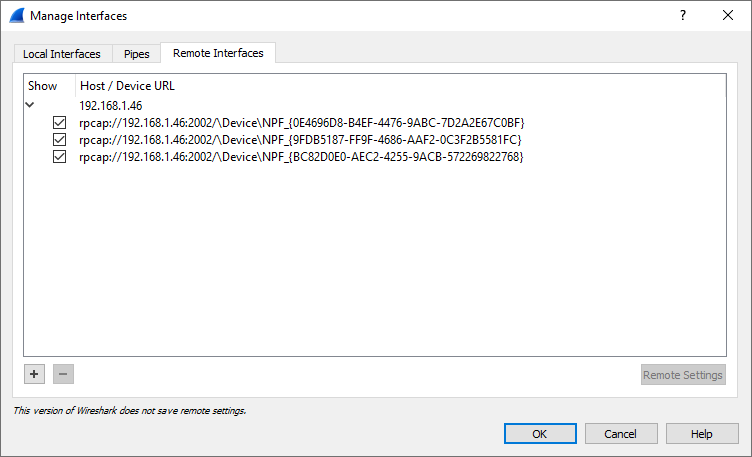
- Select "+" and add the needed information.
- The following result appears. Confirm this window.
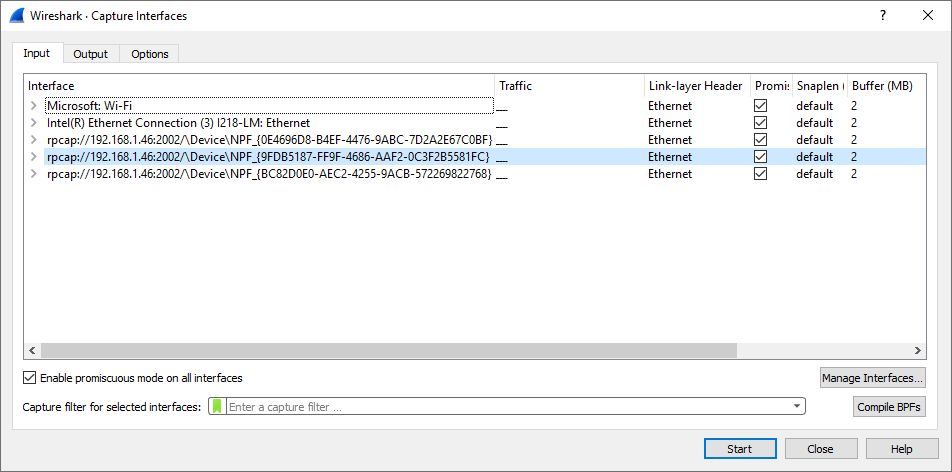
- Look for the right interface and start the capture.
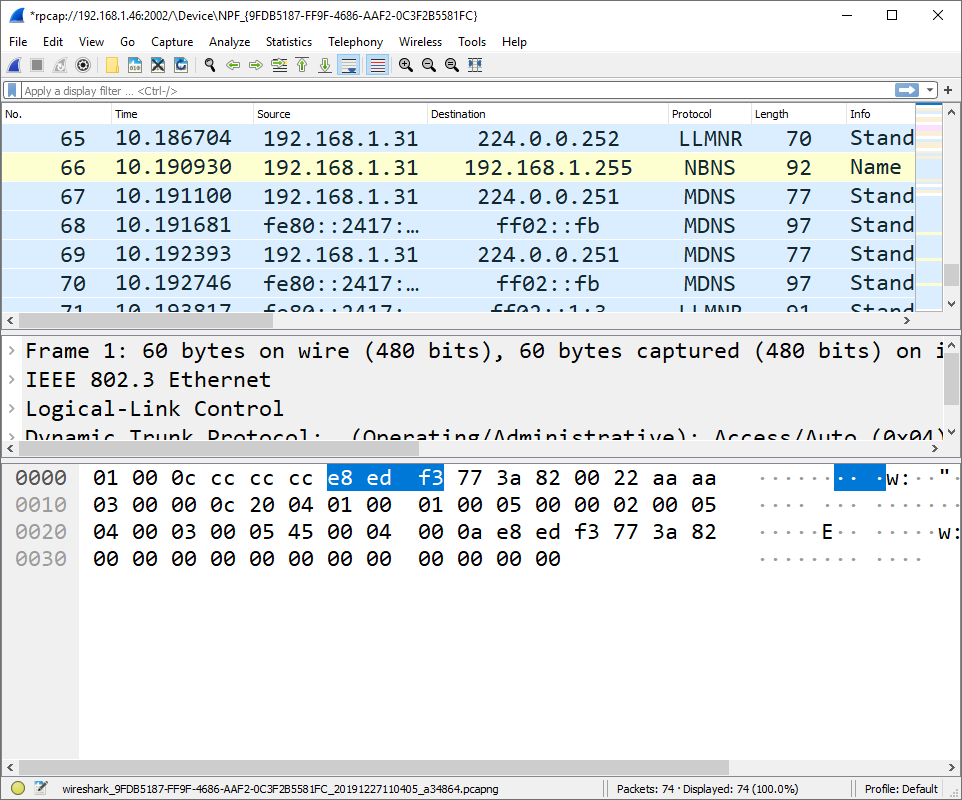
- The result is a succesfull remote capture.
Conclusion
- Besides the regular capturing methods (SPAN, TAP, HUB,... ) this method also provides some possibilities.